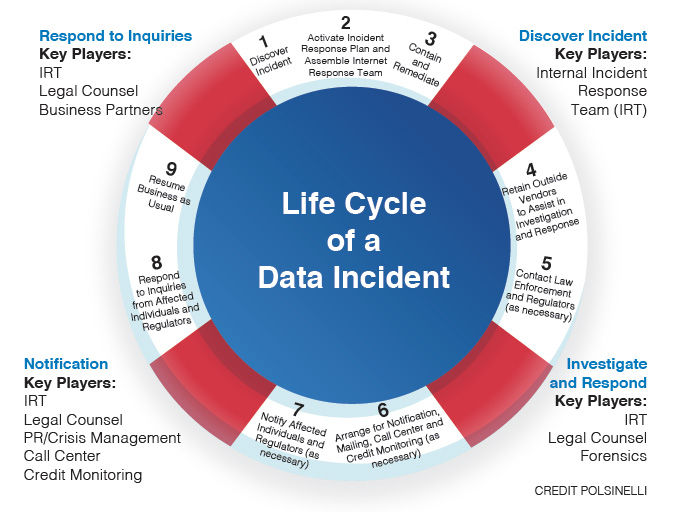
A chart, developed by law firm Polsinelli, on the life cycle of a data incident. CREDIT POLSINELLI
By Katharine Carlon
[email protected]
Whether it’s a ransomware attack, extortion, straight-up theft or a “flavor of the day” Office 365 business email compromise, attorneys who’ve helped shepherd clients through hundreds of data incidents say the threat is growing – and everyone is vulnerable.
“In terms of the size of companies getting hit, unfortunately it’s everyone,” said Bruce Radke, an attorney with law firm Polsinelli, who along with colleague Martin McElligott spoke about recent trends in data incident response at the CBJ’s Cyber Security Breakfast on Sept. 5. “We see a lot of unsophisticated threat actors who are engaged in ‘straying and praying,’ that is they will send out phishing emails to everyone, hoping someone clicks on one of those links and provides their credentials.”
And then there are the sophisticated actors, Mr. Radke said, like the ones who breached the system of a small specialty paint manufacturer and held its formula for ransom, nearly bankrupting the company, or the hackers who dropped ransomware on a public utility then flaunted their mastery of the network by sending a ransom letter to the chief information security officer’s printer.
“Over the last 18 months, we’ve seen a shift in what the threat actors are focusing on,” Mr. Radke said, adding that simply harvesting Social Security and credit card numbers has become old hat for many. “More sophisticated folks will get into your network, understand your network and then either drop some ransomware or grab some information from you. And at that time, rather than selling that information, they ask for money.”
Mr. McElligott said that, by far, most of the threats Polsinelli’s legal team currently see revolve around phishing schemes – most prominently the Office 365 email compromise – which depend on unsuspecting users opening a OneDrive, Google Drive or Dropbox document and entering their credentials for a criminal to then exploit.
In some cases, that gives them access to entire databases of employee W-2s “and it’s a race to TurboTax to file those returns.” In others, he said, they are “getting into the box, watching behavior, knowing the chain of command and getting the OK to send wires out,” resulting in more than $25 million out the door for Polsinelli clients since alone December.
Malware and brute force password attacks remain threats. But it is the rise of ransomware attacks, extortion and theft or destruction of digital assets that is the stuff of corporate nightmares.
“Sometimes it’s a threat to go public with certain info and other times we’ve seen where they might manipulate a formula,” Mr. McElligott said. “Say you’re producing a paint or a baby formula. The threat actors can get in, manipulate the formula as it’s being made, and you get a little note saying, ‘hey, there’s about five pallets of baby formula that’s a risk to your customers. Pay the ransom, otherwise we’re not going to tell you which pallet that is, and if you don’t pay it and it gets out there and someone gets sick, we’re going to let them know that you knew.’”
Whether it’s a minor phishing attack or a company-threatening extortion attempt, Mr. Radke said the steps to mitigating and resolving the issue remain mostly the same, although the costs of containment can vary significantly – from about $9,000 for outside forensics and legal costs for an email compromise with just one account affected to between several hundred thousand and a $1 million for a major network intrusion or ransomware event.
“First, you need to develop your instant response team so you can handle the typical incident and all sorts of variations,” Mr. Radke said, adding that once an issue is detected, the team should be assembled, and investigation and remediation of the incident set into motion. Often, he said, that will entail hiring an outside forensics team specializing in instant response and data breach investigations as well as legal advisers.
“We kind of take a step back and let forensics find out what happened,” he said. “At the same time, depending on the nature of the circumstance and who we’re dealing with, both in terms of our clients and the threat actors, we may want to reach out to law enforcement and regulators and say, ‘hey, something’s happening here.’”
Mr. McElligott said that once forensics identify the scope of the issue, the legal team begins working through state notification laws and determining whether notification letters will be handled in-house or outsourced, as well as whether the company will need to offer its customers credit monitoring.
“It doesn’t necessarily end with notification,” he said. “There’s going to be follow-up with clients and follow-up with regulators. There are certain AGs that we never hear from and then there’s others that are frequent fliers, and they’ve got a question, no matter how small or how contained the incident is.”




